Effective IT Risk Management.
Businesses today are reliant on IT. But have you ever thought about the implications of not having a working phone, not being able to process orders, losing customer data or even losing your IT equipment in a flood?
These are the very real risks that business owners and IT managers face every day. Without effective IT risk management, the consequences of these risks could be catastrophic for your business. Knowing how to assess and mitigate risks is the key to success, but understanding where and how to start can be a little overwhelming. We’ve put together an extensive guide to effective IT risk management. Here we’ll cover everything from understanding the risks, how to do an assessment and where to get help.
What is IT Risk Management?
IT Risk Management is the process of identifying, monitoring and managing risks that could negatively impact on the operation of your organisation.
If your business is reliant in IT there is always the potential for something to go wrong.
In our experience, IT risk is frequently ignored or passed on to junior staff, without thought for the real implications. And these implications can be huge! If your IT fails for whatever reason, you could lose public credibility, or customers. Worst still a loss of productivity could result in complete business closure.
That’s why understanding your perceived risks and having a system in place is the best way to minimise negative impacts when things go wrong. Failure to consider the risks could be catastrophic.
What Are The Different Types of IT Risk?
IT can go wrong for several different reasons. Here are some of the most common problems that can occur.
- System failure: A failure with either your device or hardware, or operating system software. Failures may result abnormal system behaviour or it may run inefficiently.
- Human Error: This may include accidentally deleting files, or customer data. Opening a phishing email resulting in a data breach
- Cyber Attacks: These include viruses, malware, ransomware, phishing and device vulnerability and weak passwords.
- Natural Disasters: Damage to equipment caused by hurricanes, earthquakes and flooding.
- External factors: In the age of Covid, planning for a pandemic is essential. How prepared is your organisation to work remotely if another outbreak occurs?
Now that you have an understand of the types of IT risks you need to consider the impact these risks have on the operation of your business.
How to Assess IT Risks?
When assessing IT risks, you need to consider both the likelihood and impact of losing your IT systems. You will also need to know what your potential risks are and what can be affected. To do this we recommend doing an Audit of your hardware and software.
Likelihood or probability of IT Risks
These can be categorised in the following way:
Low probability – the probability of this risk affecting the business the extremely low (less than once every 5 years)
Medium probability – the probability of this risk affecting the business is slight (once every 3-5 years)
High probability – the probability of the risk affecting the business is extremely high (once every year)
Impact Analysis of IT Risks
Once you’ve identified the perceived risks within your organisation and determined the probability of each risk, you should then consider the kind of impact each risk would have on your organisation.
For example, which parts of the organisation would be affected as a result of a cyber-attack?
Each risk will fall into one of these categories:
Low impact – a low impact risk which can easily be managed and have little to no impact on the business, staff or operations.
Medium Impact – a medium impact risk will significantly affect the business, staff or operations
High Impact – a high impact risk will cause catastrophic failures and may force the organisation to terminate project, departments or operations.
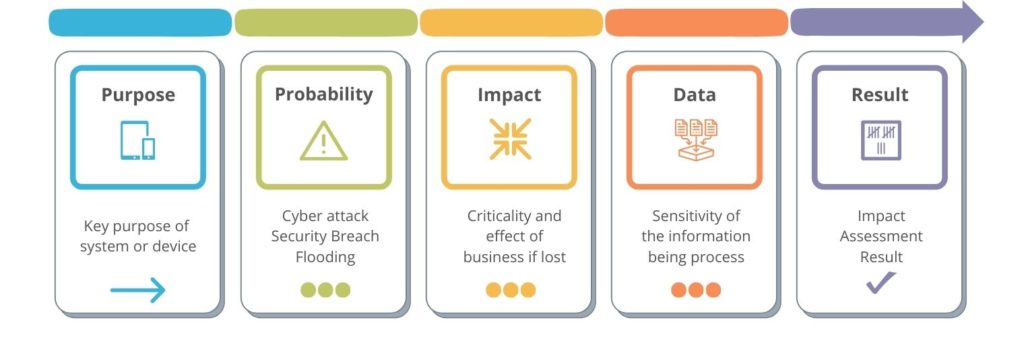
A great way of determining risk impact is to consider the wider implications. Instead of looking simply at perceived risk and likelihood we also consider the purpose of the system (or device) as well as its impact on business and sensitivity of the information being processed.
Impact Assessment = Key purpose of system + Criticality & effect of business if lost + the sensitivity of the information being processed.
This helps when considering the more detailed aspects of IT or Cyber Security threats and you need to manage the risk.
Top Tip
When assessing your IT risks it’ important to think about all of your electronic and phone communications, your data and where all this is processed, handled and stored. In its simplest form, this is an assessment of the threats and vulnerabilities and their likely impact on the business.
We recommend being as holistic as possible. Examine the whole company, all stakeholders, supply chains and customers. You can go further by looking at your marketplace and the wider factors in the economy. In this way, you are considering the widest set of factors that will be determining your current risks. Now you can bring your focus back to the IT and communications and consider how these technologies are currently being use in your company, how they might be contributing toward risk or helping you mitigate them.
What to Consider When Assessing IT Risks
It Threats
Focusing on key systems, their architecture and key components is a good starting point. Consider these systems in terms of;
Resilience – How resilient is the system in the event of failure? Are there single points of failure and does the system have or support ability for redundancy (some form of fail-over built-in)? This is going to help you consider what happens when there is a failure.
Reliability – This refers to how often the system fails or how reliable it is to use and operate. You might come across technical terms like MTBF (Mean Time Between Failures), which tells you the likelihood of a failure every x-number of days.
Recovery – Now think about the types of failure and how you can recover from these. This might include hardware and where you can get it, software and how you can restart or re-install it or cloud systems where you might be reliant upon someone else recovering it for you.
Age / Life Cycle – All IT systems have a product life cycle, that sees new systems adopted and developed and older systems passing maturity and reaching obsolescence or end-of-life. Think about where your system sits within this life cycle and consider what threats that present and how it impacts issues like recovery and operation.
Support & Operation – Consider the threats around supporting and operating IT systems, such as staffing, skills ad coverage by geography and time. Are these impacted by some of the factors above, such as life cycle or do they impact recovery.
As you may be starting to see, many of these factors are closely linked. Thorough understanding of these issues is only going to improve your chance of reducing and managing your IT risk.

Cyber Threats
It seems cyber-threats are constantly on the rise and their impacts ever more damaging in terms of business impact and reputation. There is a lot of IT jargon and specialist names / terminology in this area, but here is my simple way of looking at some of these threats;
Technical – Think about the IT technology around the systems you are looking at. This includes where, how and what technology they use directly and in-directly. How do they interact or work on the back of other systems? This can help you simplify what you are looking at and how you think about the threats or risks present. i.e. You have a cloud-based application, that is accessed by office and home workers. You will need to consider the endpoints (computers), infrastructure (networks, firewalls, etc.), hosting (servers & data centre) and software (application). In this way, you set-up the ‘chain’ of elements forming the end-to-end process.
Human – Now think about the people, how they behave and use systems. You might consider what is input to systems and what is not, what is written down, etc. This is a difficult area and any analysis is likely to only factor in some of the issues. However, you can easily do a sample check, ask questions and get a feel for how these factors could contribute toward risk. Don’t forget, its not always the technology that presents the risks!
Testing – Look to see if potential vulnerabilities in IT systems have been evaluated or tested. Is regular vulnerability testing (generally automated scanning & reporting) done? Is it necessary to go further and look at Penetration Testing (generally involving a human performing tests)? Pen Testing can also look at software & applications or look at networks / firewalls and infrastructure. But this then gives you quantitative / hard data to work with.
Get more information from the National Cyber Security Centre.
Quantitive and Qualitative
Quantitative – These are the hard numbers, such as financial costs of impact (Profit or Loss) or costs of remediation such as ROI (Return on Investment). They can also include facts and figures regarding performance (MTBF) or operations (SLA – Service Level Agreements).
Qualitative – This moves us towards how people feel about or perceive things around IT risk. This can include public or customer perception following a cyber-breach, shareholder confidence from poor press coverage, etc.
It risk management framework
Types of risk management
At its very basic level, managing risk can only be avoided, reduced, transferred or accepted. Let’s look at each one:
IT Risk Avoidance – This means not doing something or side stepping an action to avoid triggering the associated risk. In terms of IT, this might be avoiding in-house software development in favour of off-the-shelf solutions; For telecoms, it might be preventing call recording to avoid credit card details being held; In the areas of cyber-security, it maybe not allowing ‘bring-your-own-devices’ due to the potential data risks.
Reducing IT Risks – This is often commonly done when upgrading or improving IT or communication systems. Upgrading the old server with new improved unit, migrating to the cloud or deploying better malware protection are all ways to reduce risk and of course also have other business benefits.
Transferring IT Risks – Moving the risk to something or someone else is the third way to manage risks and often means moving the responsibility, but not necessarily the impact of the risk. Examples here might include outsourcing your IT support function or moving the storage and processing of data from in-house to the cloud.
Accepting IT Risks – The final way the manage IT risk, is to understand and accept it. There is always some form of risk and what’s considered acceptable becomes the key question. Acceptable risk can be thought of in terms of how much downtime, how long an outage or what is the recovery plan following a disaster?
In these risk management methods, IT and business knowledge are needed to make the best decisions. Considering risks and their management can only be done by understanding impact and the associated costs. This means a wider knowledge of the business and keys key processes. Once you know this you can begin to build a process around business continuity and disaster recover.
Uncertainty
There can also be areas of uncertainty around managing IT risk as we try to determine the likelihood of something happening, its direct and in-direct impacts or changes in the internal or external environment. Firstly, you have to start somewhere and then adopt an on-going process of improvement and refinement. Therefore, little and often, regular reviews can help to reduce this uncertainty.
IT Risk Management: Planning & Strategy
In small and medium sized business, the process of IT risk management can run closely alongside IT planning and strategy. For many smaller companies, formal planning and strategy is not feasible or favoured and here we recommend an on-going process of IT road mapping and continuous IT improvement. IT risk management is then incorporated into regular review processes, thinking about recent issues or problems and changes. This on-going style planning becomes similar to Lean or Agile systems, with a plan, do, check and act form, that creates a continuous process of improvement.
Compliance & Standards
The purpose of standards such as Cyber Essentials, ISO270001 & ITIL are all about helping to reduce risk, through improved processes and standards that lead to better outcomes. Therefore, look at these types of standards as ways to reduce IT risk through best practice. For example, the base-level device reporting needed in Cyber-Essentials, ensures your device hardware & software are operating to the minimum supported standards. The associated benefits, such as free inclusive cyber-insurance, better quality, stronger processes and reduced errors are also contributing to better risk management.
However, also be mindful of the gaps in these standards, such as the annual nature of Cyber Essentials certification, virus the need for on-going continuous monitoring. i.e. don’t think that getting an annual certification removes the on-going risks! Therefore, we see a trade-off between the reduction in risk virus the cost of that reduction, which is a constant concern for all businesses.
The Human Element
We mentioned earlier the human element in cyber-risks and this applies in the wider IT risk management process. Often there are many stakeholders / people involved and its worth considering how individuals or groups are thinking, how factors like self-interest, group think, bias & different perspectives impact your risk management. This makes it hard to fully agree on IT risk and how it should be managed, but by focusing on talking, communicating & collaborating as much as possible, common ground can be found. Finally, try the KISS (Keep It Simple Stupid) principal.
Operation
We have mentioned how IT risk management is linked to planning & strategy, but we should also consider the operational side of things too. Change is a continuous process in both IT and business and being mindful of this, in regard to risk can be useful. In larger companies, formal Change Management processes aim to address this by considering change, its impact, backout plans and stakeholder communication. Even in small and medium business, this can be useful but can be done in a much more informal way. Simple ticketing systems, email communications and regular meetings can replace much of the systems seen in bigger companies.
Benefits of IT Risk Management
IT risk management give you the chance to mitigate risk and prepare for the worst. Here are just some of the many benefits of conducting regular risk assessment and ongoing risk management.
1. Identifies way to minimise risks
We often find that many risks can be minimised when they are identified. For example, if you know your business is under threat from phishing emails, give your staff adequate training. You may also want to establish tighter policies that your staff should adhere to.
2. Opportunity to Develop Risk Responses
A Risk response allows you to take your high priority risks and decide how to treat them. You may decide to implement strategies that will minimise risks making them a lower priority risk.
3. Reduce Costs
Downtimes or outages can be disastrous for the business. Not only can they result in a loss of customer trust, they effect efficiency, communications and even sales. Understanding the risks will allow you to work towards minimising them. Whether that means updating systems or employing help through IT Consultancy. Taking the necessary steps to keep everything up and running will inevitably reduce costs in the long run.
4. Gain Trust of Customers and Stakeholders
Losing data for whatever reason can be catastrophic for businesses. Data Theft is another serious and real issue facing many organisations. Building customer trust and being able to prove the steps you stake to protect customer data is vital. If you’re able to gain customer trust you’ll certainly gain customer loyalty.
Need help With IT Risk Management?
All of our services are specifically aimed at small & medium sized business. We can help with IT risk management through our range of consultancy, planning and strategy solutions. These one-off activities start with auditing technology & business processes and can include the detailed planning around road mapping and planning change to reduce IT risk.
For many customers we provide an on-going set of managed services and IT support functions, including Cyber Security Managed Services that help minimise IT risks through regular proactive monitoring and support. This can include vulnerability scanning, which is included in our security & risk reporting service, system health checks and business focused risk reporting and regular auditing.
We also provide the technical solutions, such as cyber-security anti-virus, malware protection through to 24*7 threat monitoring and detection. Design & Implementation, such as network upgrades, cloud telecoms systems or bespoke software systems can also be provided.
Finally, we can assist with certification and standards such as Cyber Essentials, Cyber Essentials Plus and Penetration testing. In this way we can help most small and medium businesses by providing a complete end-to-end solution.
If you have any questions about this guide or want to talk to one of our consults about IT Risk Management, then please contact us.
Stay Connected
Subscribe for monthly tips and resources on how to transform your business through technology.
Business Resources
Contact Charlton Networks
Transform your IT systems.
Contact us today for a free consultation.